7. Firewall
What is Firewall
- It is a part of computer system or network designed to stop unauthorised traffic flowing from one network to another.
- Separate
trustedanduntrustedcomponents of a network. Differentiatenetworks within a trusted network.- Main functionalities are
filtering data,redirecting trafficand protecting againstnetwork attacks
Requirements of a firewall
- All the traffic between trust zones should pass through firewall.
- Only
authorizedtraffic, as defined by the security policy, should be allowed to pass through. - The firewall itself must be immune to penetration, which implies using a
hardened systemwith secured Operating Systems.
Firewall Policy
User control: Controls access to the data based on the role of the user who is attempting to access it. Applied to users inside the firewall perimeter.Service control: Controls access by the type of service offered by the host. Applied on the basis of network address, protocol of connection and port numbers.Direction control: Determines the direction in which requests may be initiated and are allowed to flow through the firewall. It tells whether the traffic is “inbound” (From the network to firewall) or vice-versa “outbound”
Firewall actions
Accepted: Allowed to enter the connected network/host through the firewall.
Denied: Not permitted to enter the other side of firewall.
Rejected: Similar to “Denied”, but tells the source about this decision through ICMP packet.
Type of filters
Depending on the mode of operation, there are three types of firewalls :
- Packet Filter Firewall
- Stateful Firewall
- Application/Proxy Firewall
Packet Filter Firewall
- Controls traffic based on the information in packet headers, without looking into the payload that contains application data.
- Doesn’t pay attention to if the packet is a part of existing stream or traffic.
- Doesn’t maintain the states about packets. Also called Stateless Firewall.
Stateful Firewall
- Tracks the state of traffic by monitoring all the connection interactions until is closed.
Connection state tableis maintained to understand the context of packets.
Application/Proxy Firewall
- Controls input, output and access from/to an application or service
- Acts an
intermediarybyimpersonatingthe intended recipient. - The client’s connection terminates at the proxy and a separate connection is initiated from the proxy to the destination host.
- Data on the connection is analysed up to the application layer to determine if the packet should be allowed or rejected.
You get the most control over the application firewall, but more computation heavy because you are actually impersonating a client.
Building Firewall using Netfilter
Packet filter firewall implementation in Linux
- Packet filtering can be done inside the kernel.
- Need changes in the kernel
- Linux provides two mechanisms to achieve this :
- Netfilter: Provides hooks at critical points on the packet traversal path inside Linux Kernel.
Loadable Kernel Modules: Allow privileged users to dynamically add/remove modules to the kernel, so there is no need to recompile the entire kernel.- You are not compiling entire kernel but more like compiling a library that the kernel use
Netfilter
- Netfilter hooks are rich packet processing and filtering framework.
- Each protocol stack defines a
series of hooksalong thepacket’s traversal pathin the stack. - Developers can use LKMs to register
callback functionsto these hooks. - When a packet arrives at each of these hooks, the protocol stack calls the netfilter framework with the packet and hook number.
- Netfilter checks if any kernel module has registered a callback function at this hook.
- Each registered module will be called, and they are free to analyze or manipulate the packet and return the
verdicton the packet.
Verdict (Return Values)
It is something you can return after analysis is done on the packet
NF_ACCEPT: Let the packet flow through the stack.NF_DROP: Discard the packet.NF_QUEUE: Pass the packet to the user space via nf_queue facility.NF_STOLEN: Inform the netfilter to forget about this packet, The packet isfurther processedby the module.NF_REPEAT: Request the netfilter to call this module again.
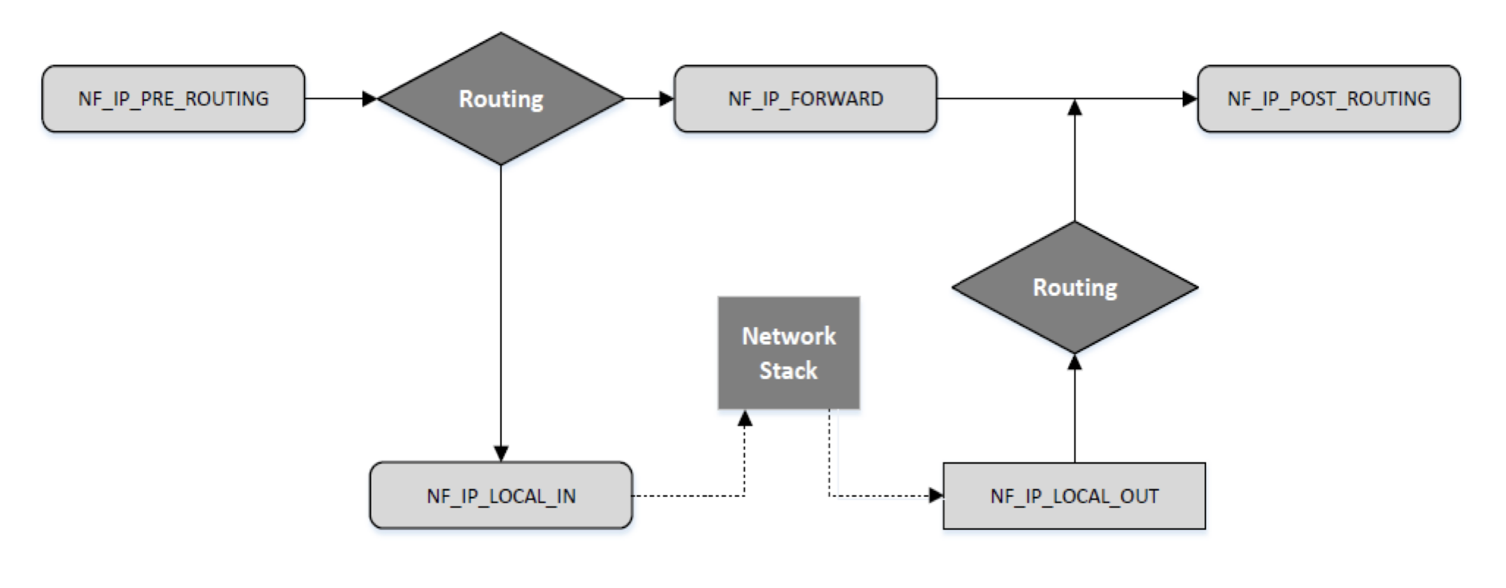
#toupdate redraw, network stack is the os model, remove the header, first routing decide if its meant for local machine, second routing filter the actual packet payload. The prerouting is the function that you defined
Iptables Firewall in linux
It is a set of predefined rules for you to use
- Iptables is a built-in firewall based on netfilter.
- Kernel part: Xtables
- User-space program: iptables
- Usually, iptables refer to both kernel and user space programs.
- Rules are arranged in hierarchical structure as shown in the table.
Iptables Firewall - Structure
- Each table contains several chains, each of which corresponds to a netfilter hook.
- Each chain indicates where its rules are enforced.
- Example : Rules on FORWARD chain are enforced at NF_IP_FORWARD hook and rules on INPUT chain are enforced at NF_IP_LOCAL_IN hook.
- Each chain contains a set of firewall rules that will be enforced.
- User can add rules to the chains.
- Example : To block all incoming telnet traffic, add a rule to the INPUT chain of the filter table
Traversing Chains and Rule Matching
Tables and Chains: Within Netfilter, packets are processed by tables. Each table contains a series of chains, which are essentially ordered lists of rules. There are predefined chains like INPUT, FORWARD, and OUTPUT, and users can define custom chains. Each rule in a chain inspects the packet and decides an action, like accepting or dropping the packet.
- Filter Table: The primary table used for filtering packets. It contains the INPUT, FORWARD, and OUTPUT chains.
- NAT Table: Used for Network Address Translation (NAT). Contains chains like PREROUTING and POSTROUTING.
- Mangle Table: For packet alteration.
Chains: refer to a series of rules used to determine what to do with network packets. Chains are essentially ordered lists of rules that packets are checked against sequentially.
There are three predefined chains in the filter table of iptables:
- INPUT: This chain is used to process packets that are destined for the local system.
- FORWARD: This chain is used for packets that are routed through the local system but aren't meant for the local system itself. Typically, this is used when the system acts as a router or gateway.
- OUTPUT: This chain is used for packets that originate from the local system.
Apart from the filter table, there are other tables in iptables, such as nat, mangle, and raw, and they have their own predefined chains. For example, the nat table includes:
- PREROUTING: For altering packets as soon as they come in.
- POSTROUTING: For altering packets as they are about to go out.
- OUTPUT: For altering locally-generated packets before routing.
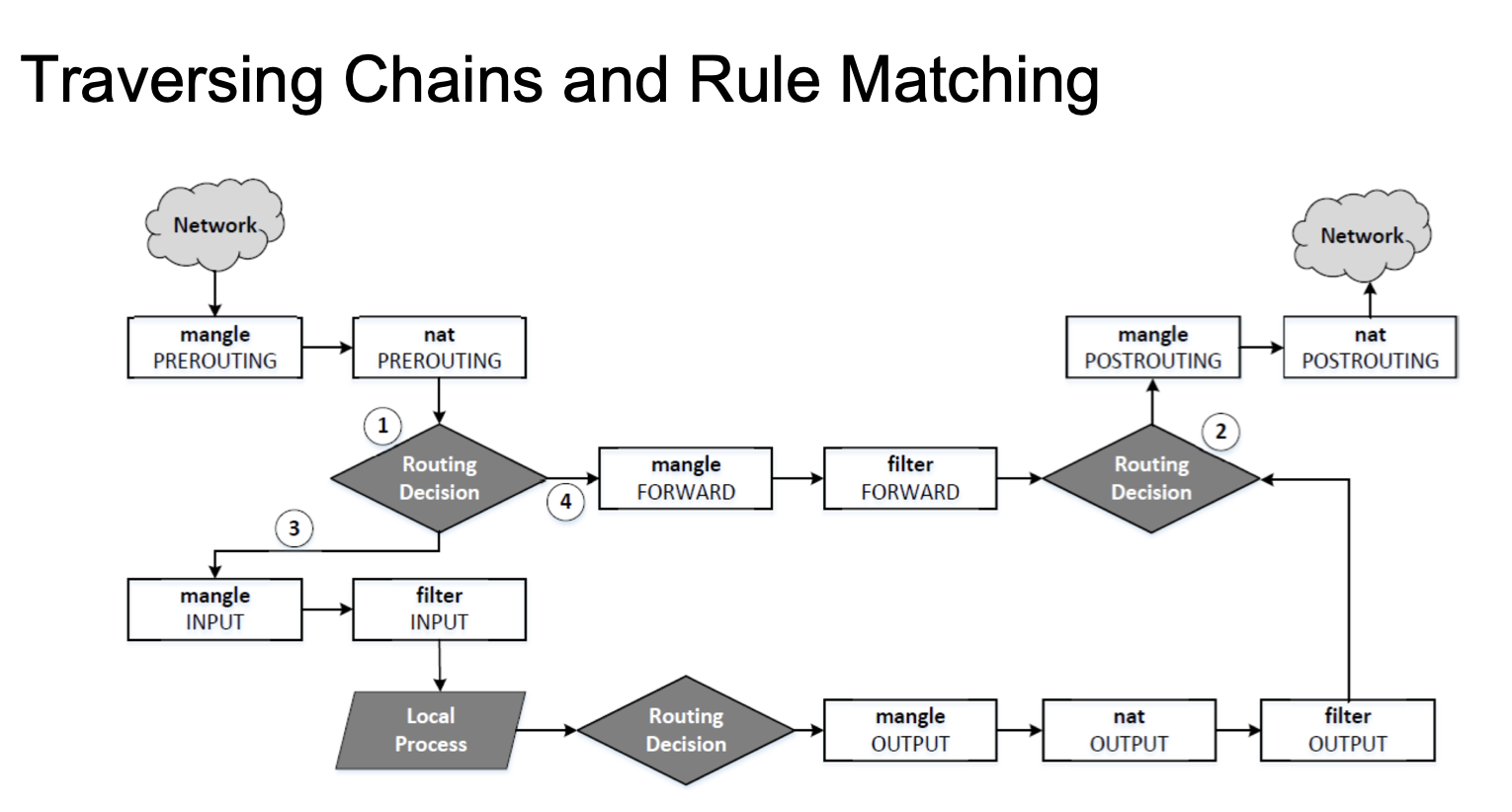
- Decideds if the final destination of the packet is the local machine
- Packet traverses through
INPUTchain - Packet traverses through
FORWARDchains - Decides. from which of the network interface to send out outgoing packets
As a packet traverses through each chain, rules on the chain are examined to see whether there is a match or not. If there is a match, the corresponding target action is executed: ACCEPT, DROP or jumping to user-defined chain.
Increase the TTL field of all packets by 5.
Add a rule to the mangle table and choose a chain provided by netfilter hooks. We choose PREROUTING chain so the changes can be applied to all packets, regardless they are for the current host or for others.
iptables -t mangle -A PREROUTING -j TTL -ttl-inc 5
Iptables Extensions
Iptables functions can be extended using modules also called as extensions.
Examples:
Conntrack: To specify rules based on connections to build stateful firewalls.
Owner: To specify rules based on user ids. Ex: To prevent user Alice from sending out telnet packets. Owner module can match packets based on the user/group id of the process that created them. This works only for OUTPUT chain (outgoing packets) as it is impossible to find the user ids for INPUT chain(incoming packets).
Stateful Firewall using Connection Tracking
- A stateful firewall monitors incoming and outgoing packets over a period of time.
- Records attributes like IP address, port numbers, sequence numbers. Collectively known as connection states.
- A connection state, in context of a firewall signifies whether a given packet is a part of an existing flow or not.
- Hence, it is applied to both connection-oriented (TCP) and connectionless protocols (UDP and ICMP).
Connection Tracking Framework in Linux
nf_conntrackis aconnection trackingframework in Linux kernel built on the top of netfilter.- Each incoming packet is marked with a
connection stateas described:- NEW: The connection is starting and packet is a part of a valid sequence. It only exists for a connection if the firewall has only seen traffic in one direction.
- ESTABLISHED: The connection has been established and is a two-way communication.
- RELATED: Special state that helps to establish relationships among different connections. E.g., FTP Control traffic and FTP Data traffic are related.
- INVALID : This state is used for packets that do not follow the expected behavior of a connection.
- iptables can use nf_conntrack to build stateful firewall rules.
Example
sudo iptables -A OUTPUT -p tcp -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT
This command set up firewall rule to only allow outgoing TCP packets if they belong to an ESTABLISHED TCP connection
Application/Proxy Firewall and Web Proxy
- Inspects network traffic up to the application layer
- Typical implementation of an application firewall is a proxy
- Web Proxy: To control what browsers can access
- To set up a web proxy in a network, we need to ensure that all the web traffic goes through the proxy server by:
- Configuring each host computer to redirect all the web traffic to the proxy. (Browser’s network settings or using iptables)
- Place web proxies on a network bridge that connects internal and external networks.
Use proxy to bypass firewall
- Proxy can be used to evade egress filtering.
- If a firewall conducts packet filtering based on destination address, we can evade this firewall by browsing the Internet using web proxy.
- The destination address will be modified to the
proxy serverwhich defeats the packet filtering rules of the firewall.
- SSH Tunneling
- Dynamic Port Forwarding
- Virtual Private Network
SSH Tunneling
ssh -L 8000:work:23 sshmachine
Establish an ssh tunnel from Home to Remote machine that is in the firewall. The tunnel that is established will forward TCP data received on 8000 on Home to port 23 on work
Anonymizing Proxy
One can also use proxies to hide the origin of a network request from servers. As the servers can only see the traffic after it passes through proxies, source IP will be the proxy’s and actual origin is hidden
Revision question
What are the five netfilter hooks for IPv4 what are their purpose
NF_IP_PREROUTING to setup rules for packets before they enter the host machine
NF_IP_LOCAL_IN to setup rules for packets intended for the host
NF_IP_FORWARD to setuo rules for packets to be forwarded
NF_IP_LOCAL_OUT to setup rules for packets inteded for the host